Blog
Company Updates & Technology Articles

The final chapter for Aserto
Goodbye Aserto, long live Topaz.

Stateless vs Stateful Authorization
The most important design decision for an authorization system is how to bring data to the engine. Read all about the tradeoffs.
Mar 28th, 2025

AuthZEN, Gartner IAM, and native support in Topaz
OpenID AuthZEN defines an Authorization API that allows policy enforcement points to evaluate a decision in a standard way. Topaz now has native support for AuthZEN.
Feb 28th, 2025
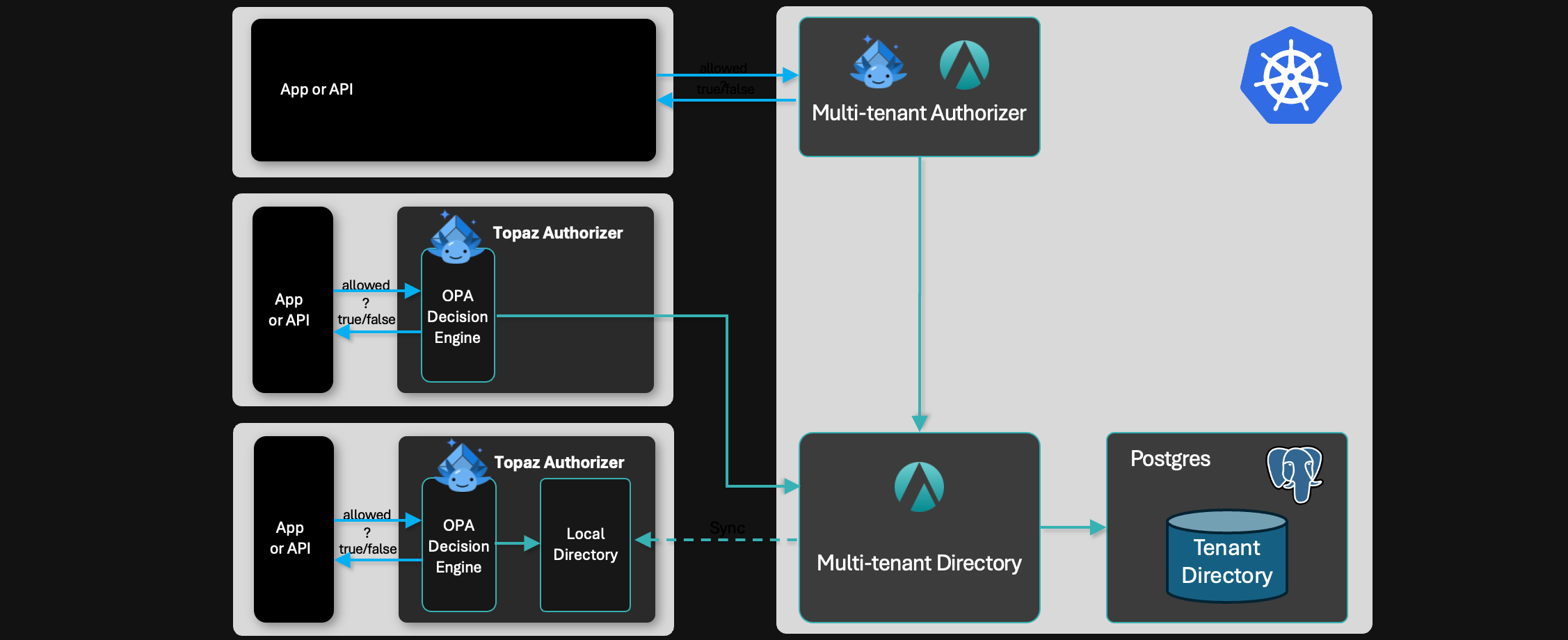
Centralized vs Distributed Authorization
What are the tradeoffs between running a central authorization service versus distributed authorizers?
Jan 24th, 2025

The Case for Centralizing Authorization
Why centralize authorization, what are the impediments, and how do you overcome them?
Jan 9th, 2025

Authorization in 2024: Year in Review
As we ring in the new year, here’s a retrospective on authorization in 2024.
Dec 31st, 2024

Authorization at Gartner IAM Summit 2024
Gartner IAM Summit is one of the top events in the identity universe, and Authorization is becoming a key pillar. Here’s our trip report.
Dec 13th, 2024
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)