Product Pulse #4: New directory and authorizer, evaluator, and more!
Over the past several weeks we’ve incrementally rolled out a few product improvements that we're excited to share with you. These include the second version of the Aserto Directory and Authorizer.
Our v2 Directory now lets you define custom object types and relation types that match your domain model. You can then associate permissions with those relation types. This opens the door for custom tailored authorization systems.
Our v2 Authorizer is now based on Topaz, the open-source project we maintain, which brings together the best of OPA and Zanzibar. The APIs exposed by the new authorizer are all rooted in /api/v2, and include OPA’s native compile and query APIs along with Aserto’s is and decisiontree APIs.
The v2 Directory and v2 Authorizer are now the defaults for new accounts and organizations.
Custom-tailor your policy to your application with the v2 Directory
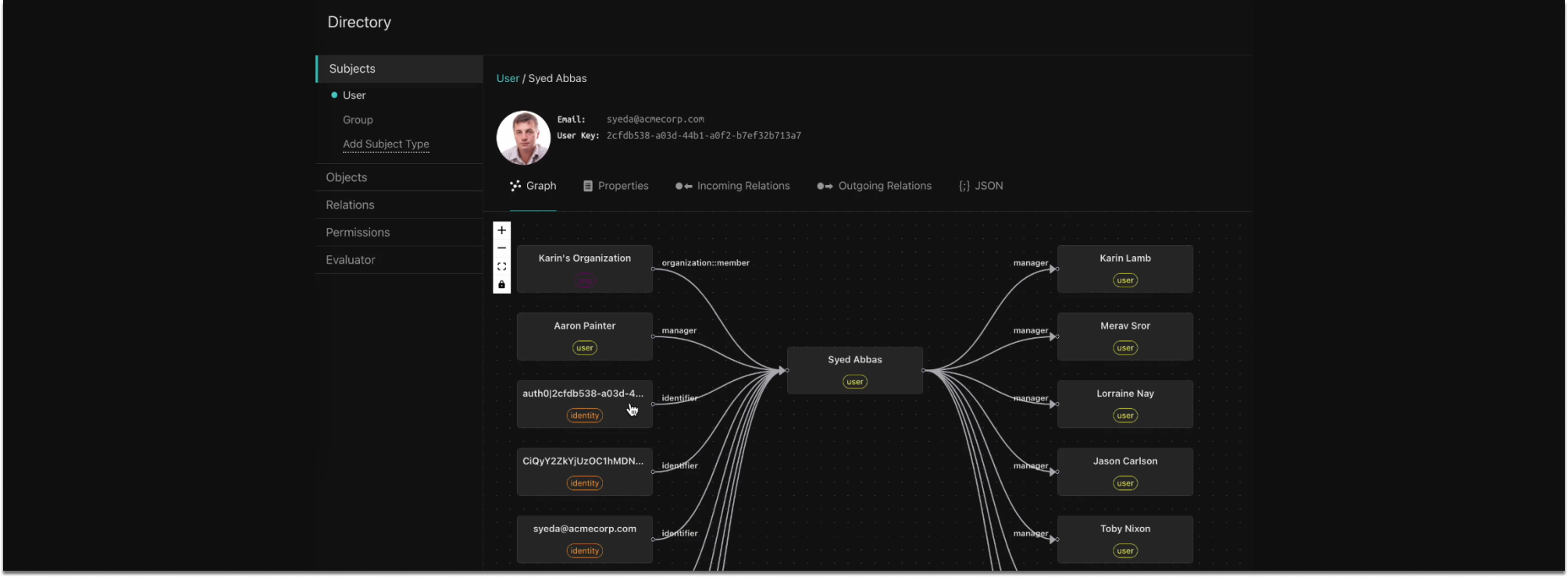
Our directory now goes far beyond the user database provided in v1. In addition to built-in support for users and groups, the v2 Directory offers a fully customizable schema for describing object types and relations based on your application’s domain model.
You can now define your own object types, the relation types that can be established between them, and the permissions associated with these relation types. This provides support for a data-centric, ReBAC authorization model.
The v2 Directory also provides the ability to custom tailor your policy to your application through a set of Rego built-ins. These built-ins can evaluate whether a user has a relation to an object instance (ds.check_relation), or has a permission on an object instance (ds.check_permission).
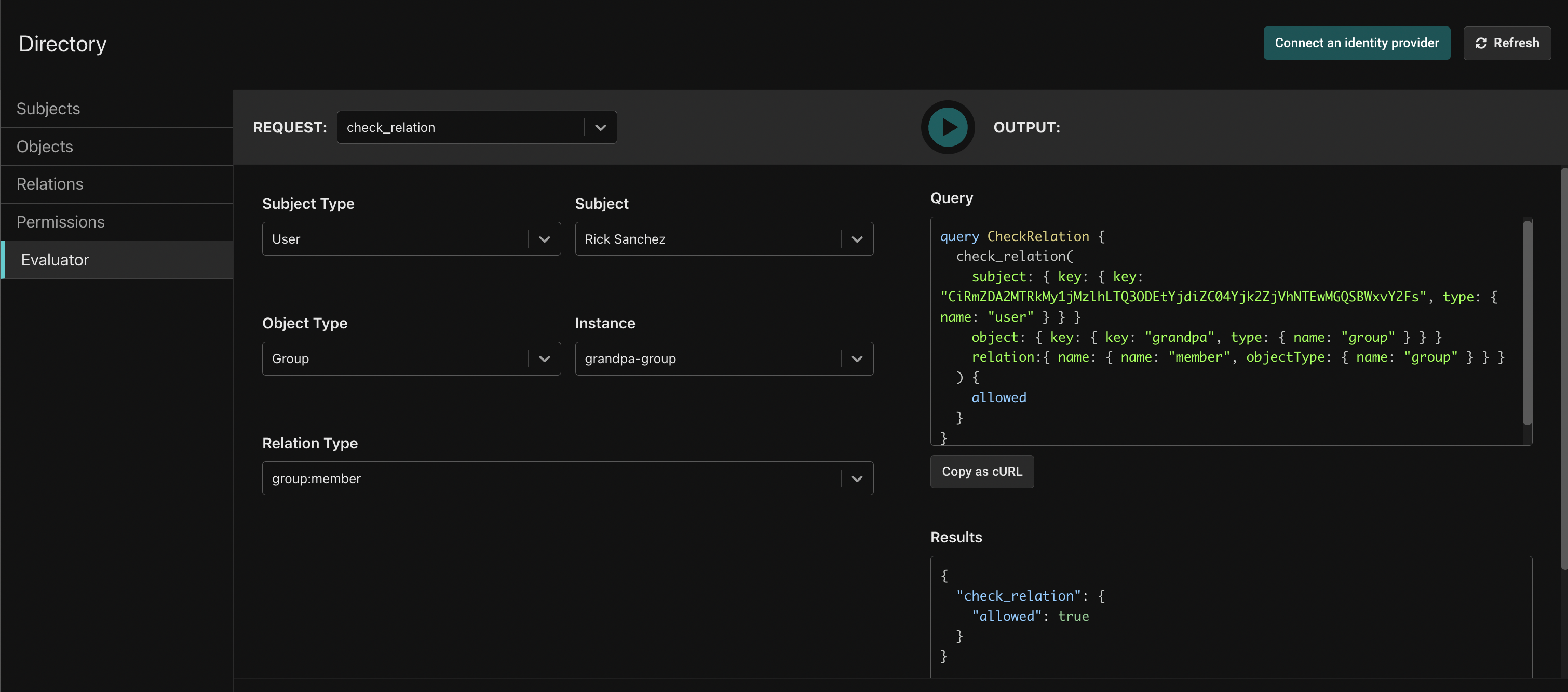
The v2 Directory now has an Evaluator tab
You can now evaluate whether a subject (user or group) has a relation or permission on an object using the Evaluator tab on the Directory page.
We currently support check_permission, check_relation, and object calls. We include a graphQL query with each call, to make it easy to incorporate into your application. You can also copy it as a cURL.
For example, we can use the check_relation call to check whether a subject has a relationship with an object. Below, we check whether Rick is a member of the “grandpa group,” and see that he is.
The v2 Authorizer
Aserto’s v2 authorization APIs are identical to those of the v1 APIs, with the following exceptions:
- The APIs all use the
/api/v2/...prefix instead of/api/v1/... - We’ve removed the id field from the policy_context, and instead created a new policy_instance object that contains the policy instance name and
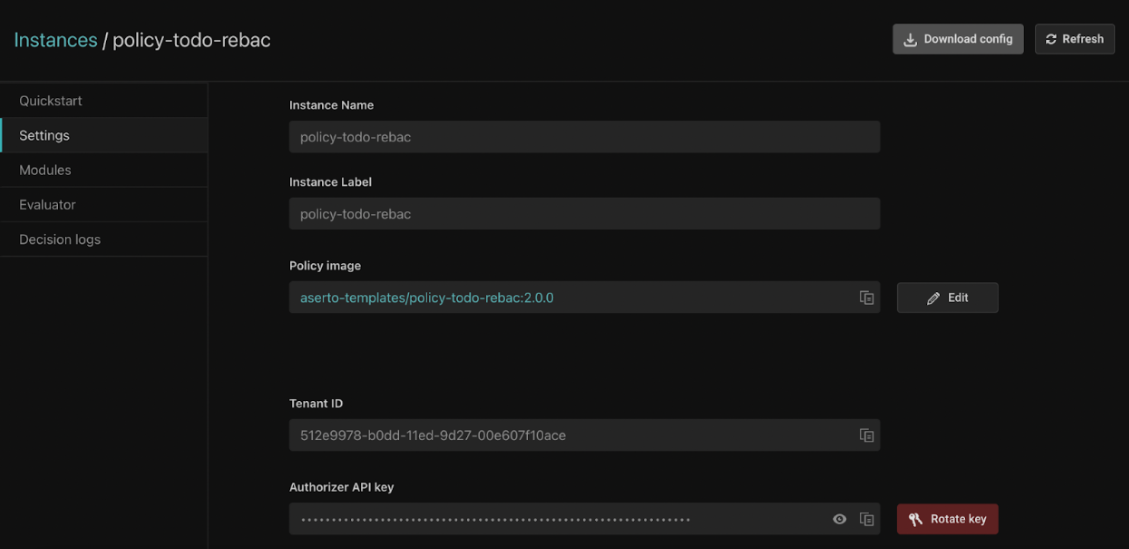
instance_label. You can find these in the policy’s Settings tab.
We've updated all our SDKs and middlewares with a “v2” branch and packages with a version number greater than or equal to 0.20. See our Ruby SDK and aserto-node npm package for examples of both.
Upgrading should be transparent, except for using the ASERTO_POLICY_NAME and ASERTO_POLICY_INSTANCE_LABEL environment variables instead of ASERTO_POLICY_ID. Use the “Download config” button in the policy's Settings page to download the v2 config, which makes it easy to migrate.
If you’re calling the REST APIs directly, refer to the documentation and specifically the upgrade page.
Managing member roles in Aserto Organizations got a bit more intuitive
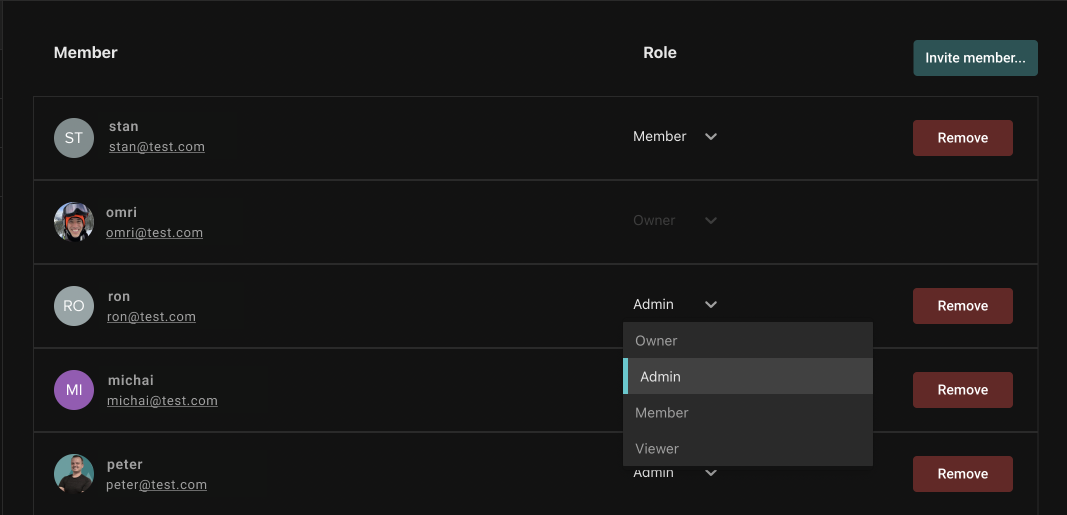
Aserto Organization owners now have an easier way to manage members. You can now update member roles without the need to click on the “Save” button. We also moved the "Remove" button into a separate table element for improved usability.
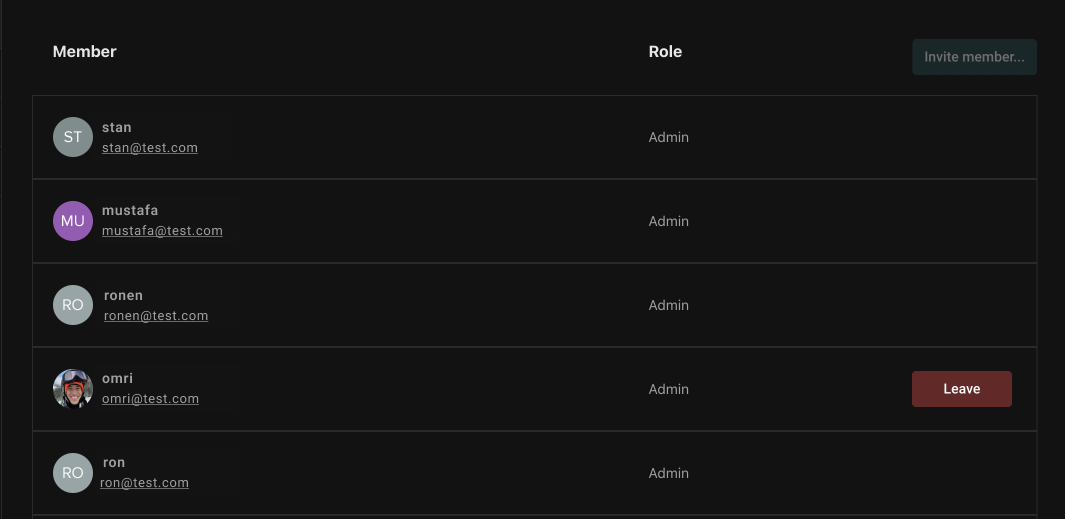
Organization members will see a display of the role each member holds. But, the only action they can take is to leave the organization.
Conclusion
Over the past several weeks we’ve rolled out a new version of our authorizer and directory. We’ve added the ability to support data-first ReBAC models and test permissions and relations between objects and subjects. We've also simplified user management for Aserto Organization admins.
Authorization is hard to build on your own! We’re building tools to make it easier for developers to implement and manage fine-grained access control.
We hope you find these updates useful and, as always, we'd love to hear from you - join our community Slack channel today and share your thoughts.
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)