Secure access for microservices and APIs
Deliver real-time access control for each microservice with a centrally managed authorization system.
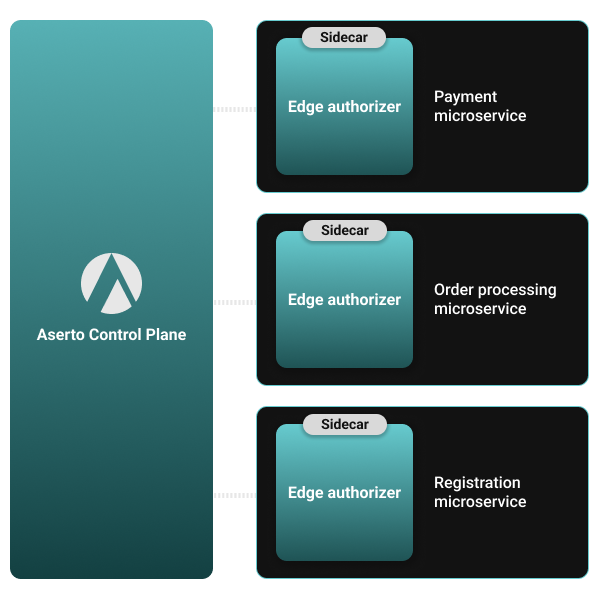



Real-time authorization for microservices, with centrally managed policies
Over the past decade, it has become best practice to break down monoliths into smaller microservices, in order to increase agility, reduce surface area in each component, improve scalability, and enhance reuse. Each microservice typically runs in its own container or pod, coupled to its own data model, and largely operates independently of the other microservices in the application.
However, when each microservice is responsible for its own authorization, it becomes difficult to add or change permissions since every service has to adapt to the change. This reduces the agility benefits that the microservices architecture provides in the first place. Aserto enables developers to lift access control logic out of each microservice and manage it centrally, providing a consistent authorization layer across all your microservices.

Every microservice makes decisions in real-time
Deliver real-time access control. Locally cached user and resource data in the Aserto sidecar enables access control decisions within milliseconds and at 100% availability.

Model your resource hierarchy
Every domain model is different; model yours in the Aserto Directory. Permissions are based on a graph of your users, attributes, resources, and relationships between them.

Evolve policy independently
Decouple policy development and feature development. Store, version, build, test, and deploy authorization policy separate from your application code.

Increase agility
Manage policy versions, updates, and rollbacks from a central control plane, across every authorizer instance.

Build on cloud-native, open foundations
Leverage an open-source tool chain and OPA-based authorizer

Explore popular authorization use cases

&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)