Product pulse #1 - Enhanced Edge Authorizer security, new ASP.NET quickstart, OPA update, and more
Jul 27th, 2022

Mustafa Branch

Our team has been hard at work improving Aserto. We’re excited to share a few of the new product improvements, onboarding features, and the implications for you, our end users. Let us know what you think!
TLDR; Authenticate Edge Authorizers with mTLS certificates. New quickstart for ASP.NET. Share your policy images with non-Aserto users. OPA and ORAS have been upgraded to more recent versions.
Securing Edge Authorizers
Aserto Edge Authorizers can now authenticate using mutual Transport Layer Security (mTLS). This new functionality ensures all the Edge Authorizers connected to your account belong to you and are provisioned by Aserto. You can create your client certificates by heading to the "Connections" tab and creating a new Edge Authorizer Connection.
This new feature improves the security of your Edge Authorizers by provisioning certificates that can expire and refresh on command.
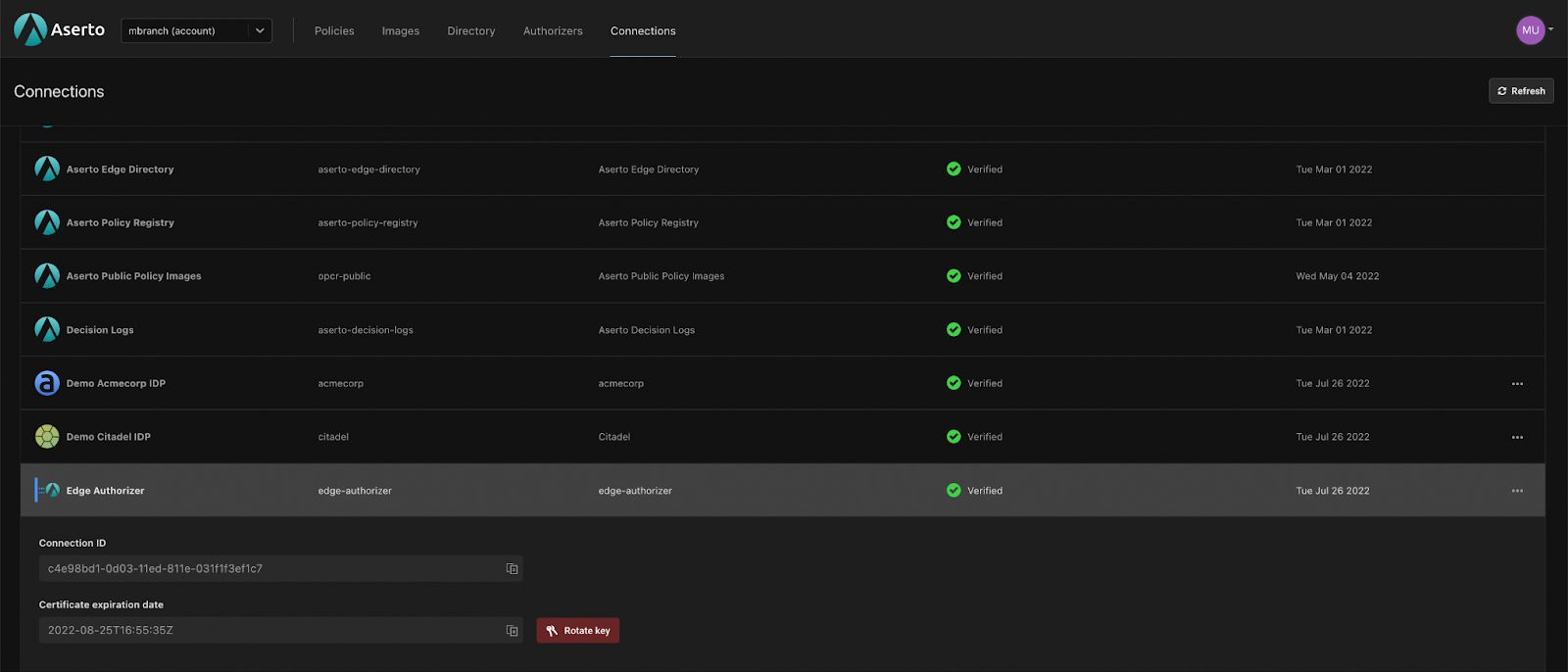
Learn how to configure your authorization certification onto Edge Authorizers here.
A new quickstart for ASP.NET Core MVC applications
You can now quickly stand up an ASP.NET app and add Aserto’s fine-grained access control with our new quickstart for ASP.NET core applications.
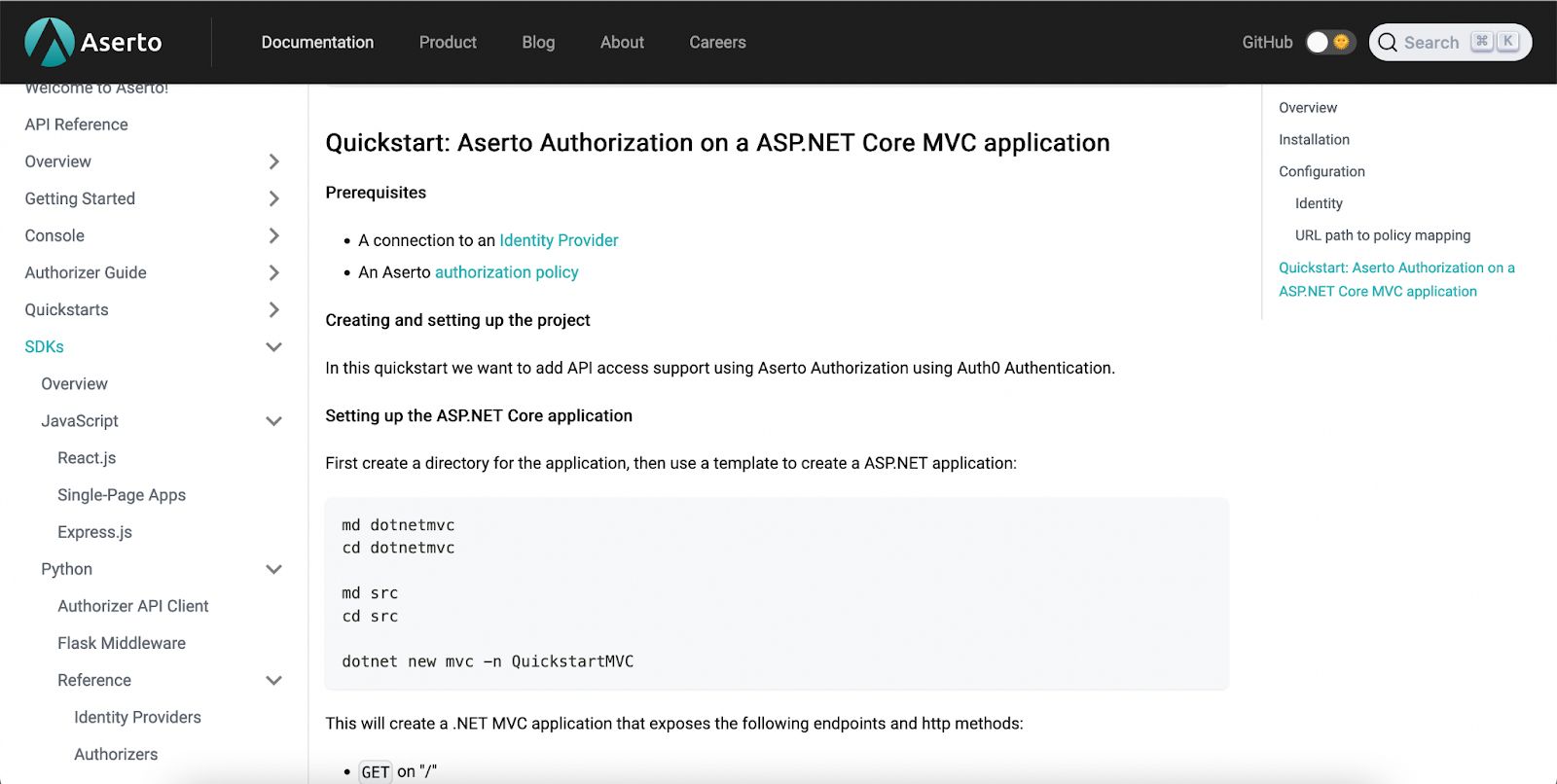
To enable authentication, you can use the Cookie and OpenID Connect (OIDC) authentication middleware that ships with the ASP.NET Core authentication package, and point it to an Auth0 account. From there, we can add the Aserto ASP.NET middleware and quickly build and add fine-grained access control policies to your application.
Easier onboarding and policy sharing
Now, anyone can list and pull policy repos from the Open Policy Registry/Aserto Policy Registry organization. This update enables Aserto to easily share templatized policy images with you, which you can use as a starting point for your authorization use case. Additionally, you can share your policy templates with others, allowing you to demonstrate how to write a specific policy.
- name: Login to OPCR
run: |
echo ${{ secrets.POLICY_PASSWORD }} | policy login -u ${{ secrets.POLICY_USERNAME }} --password-stdin
- name: Check policy signature
run: |
echo ${{ secrets.COSIGN_PUBLIC_KEY }} > cosign.pub cosign verify --key cosign.pub opcr.io/$POLICY_REPO:1.0.0
- name: Pull policy
run: |
policy pull $POLICY_REPO:1.0.0
policy save $POLICY_REPO:1.0.0 -f - | tar -zxvf -
- name: Test policy on Dockerfile
run: |
conftest test DockerfileHere’s a great example of our team sharing policy templates for automating your Conftest/Gatekeeper workflow.
Keeping OPA up to date
Our distributed authorizers and Policy CLI (an open-source toolchain for building, versioning, pushing, and pulling policy images) are built on the Open Policy Agent (OPA) and ORAS CLI projects. Previously these two dependencies were on v0.3x and v0.x, respectively. We have worked to keep these versions as close to their current release as possible and, as a result, have now upgraded OPA to v0.4x and ORAS to v1.x. Now users can take advantage of the latest features in their policy workflow.
Summary
Our team has been hard at work over the last few weeks, pushing out mTLS authentication, OPA/ORAS upgrades, and policy sharing and onboarding resources. These improvements aimed at making the experience of working with Aserto as secure, and simple as possible. Everything we build is meant to make adding fine-grained authorization easy for developers like yourself, so any and all feedback you have about Aserto would be widely appreciated. Simply drop us a line at our contact us page.
We’ll be back next month with our latest product updates. In the meantime, check out last month’s release notes, or sign up for our newsletter to get these updates in your inbox.

Mustafa Branch
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)