A CISO Perspective on Enterprise Forensics: How to Get Back From a Breach
Mar 8th, 2023

Aaron Weismann
Decision Logs

The worst day for any CISO is when their organization faces a cyber incident or breach. Gone are the days (mostly) when that would have been a career-ending event. That’s largely due to cyber incidents and breaches being a foregone conclusion for most corporations. It’s a matter of “when,” not “if.”
It’s important to know when an attack is happening, where it’s happening, and how. Even if you can’t stop the attack, that kind of information will help you quantify the scope of the attack and the potential resulting damage.
In this article, I’ll cover how authorization decision logs support a forensic review of breach events or other cyber incidents. While they’re only one component of what we should capture with a continuous monitoring program, they’re a critical component. They are also much more helpful than alternatives and can empower quick reaction and breach scoping.
How Authorization Logs Support Breach Review
Most organizations that have a continuous monitoring program in place have two basic elements to that. This first is an event correlation and alerting engine, such as a SIEM. The second is a team of people who review and respond to those alerts, such as a SOC and/or Security Analysts. This article will focus more on the former.
The quality and kind of data ingested into the SIEM will determine how you respond to a breach. If you don’t have the necessary data to identify a breach, you won’t spot or be able to respond to a breach.
Organizations typically ingest many data sources. Some of the most critical are those that identify system or network ingress and activity. For the network, that information takes the form of logs from your firewall, intrusion detection and prevention system (IDS/IPS), and secure email gateway (SEG). If you have internal firewalls and netflow information collectors, you can also spot activity once inside the ephemeral walls of an organizational network.
For applications, an ingress can be spotted with login trails or authorization logs. Login audit trails effectively provide three data points: who logged in where and when. That’s both a pro and a con. The pro is that those data points are critical to identifying improper ingress.
The con is that improper ingress is the only thing detected and only if known to be improper. There are many ways to spoof that functionality, like using legitimate stolen credentials. Additionally, once access happens, there’s no further tracking from login information. We don't know what the user does once logged in.
Authorization decision logs can provide the information needed to evaluate ingress. They can also capture the actions taken by a threat actor once in a system or data store. Authorization decision logs generated by authorization policy engines provide context around the challenge and the success or failure of that challenge. They provide a record of every access decision made for every user once they've logged in.
If the authorization policy adheres to the principle of least privilege and deny-by-default, then the authorization decision engine should reject challenges unless the authorization policy criteria are satisfied. If those criteria aren’t satisfied, a system can record:
- Who attempted access or another action,
- To what they attempted access or another action,
- When they attempted access or another action,
- What inputs were provided, and
- The criteria that were failed.
The addition of the last two data points adds significant context to authorization decision logs over login audit trails. Those data points highlight why the system denied authorization.
Additionally, login audit trails only log ingress. Authorization decision logs, if implemented to enforce least privilege and deny-by-default, should provide contextual decision information for every action taken within a system.
This level of detail provides an action-by-action tracking of a threat actor. Correlated with other data, it can provide a very accurate view of what’s going on in a system and whether those actions are legitimate. That makes an early warning system, like a continuous monitoring program, more effective.
The implications of that are staggering for any threat management team. Piecing together what an attacker’s doing and aggregating with other telemetry can let security and operations teams get ahead of attackers. It turns a reactive incident management process into a much more proactive and preventative operation. Instead of worrying about what an attacker will do next, teams can work on slowing their progress and expelling them from affected assets.
It also gives security and operations teams a quick view of the comprehensive “blast radius” of an attack.
Identifying the “Blast Radius”
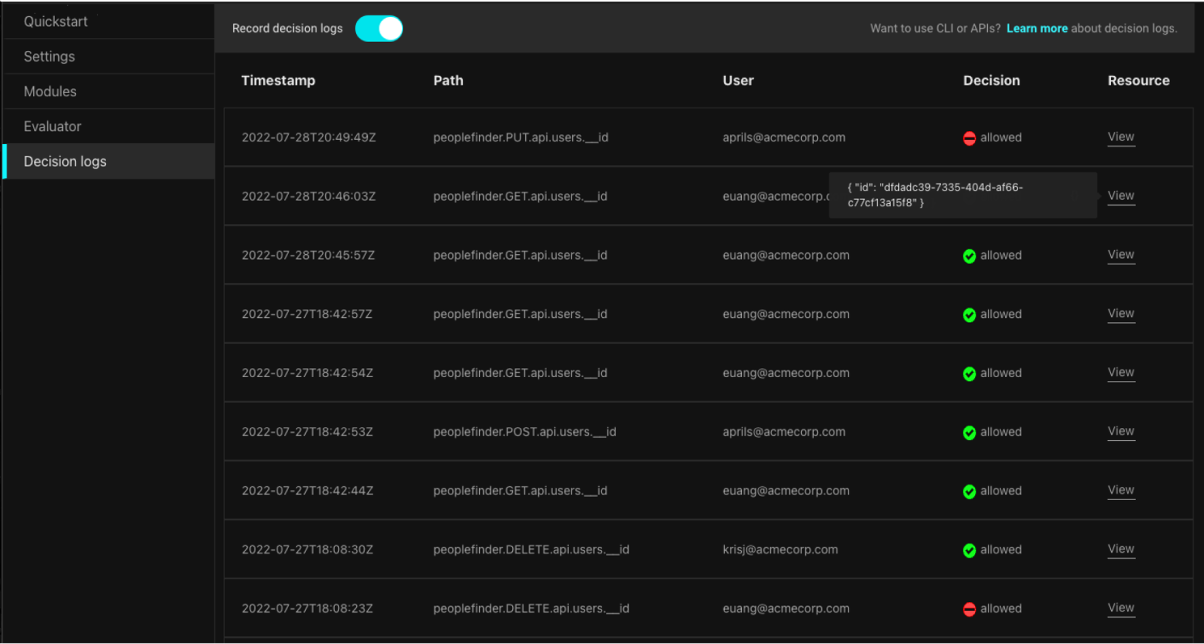
Authorization logs provide an in-depth view of the scope of a breach. In the same way that logging netflow information provides a detailed view of lateral movement through a network, access logs provide a detailed view of both lateral and vertical movement through applications and data stores.
That monitoring provides organizational incident response teams the ability to spot successful access. Combined with other logs, that will also give an idea about the extent of any data exfiltration or other forms of compromise. In other words, the full “blast radius” of an attack can be spotted quickly. If decision logs state access was granted when it shouldn’t have, then that’s in scope for the breach analysis.
Authorization decision logs can provide a view into what an attacker’s doing in nearly real-time. They can also provide a detailed forensic look-back to the entire trail from the perimeter. By capturing every access decision made, these logs provide a trail of activity that tracks a threat actor’s progress through a system.
That kind of information provides teams with robust information about what was impacted, what data could have been stolen, and how. That makes the scope of breach response and external reporting very definite. It also helps target remediation efforts to only those things that were exploited, with a hint into the root-cause of why they were exploited.
The Need for Granular Authorization Decision Logs
As a CISO, I’ll never say that I want less data. I may say that I want less bad or irrelevant data. But I’ll also say that I want as much quality relevant data as I can get my hands on. Quality data drives quality decisions. A lot of quality data drives informed decisions.
Cyber attacks and breach events tend to be somewhat pattern-based. Gaining and elevating access to many systems tend to follow a set of exploits or vulnerabilities that can be spotted by a well-tuned SIEM. That’s how most incident playbooks are generated: look for event X with Y conditions and alert on that or take Z actions.
It’s very difficult for my SIEM and team to spot and act on patterns when they lack the data points to establish those patterns. Login information is great, but it doesn’t provide the necessary granularity or specificity to pinpoint an active attack.
Authorization decision logs, however, provide real-time tracking of an attack. It lets my team know everything that’s happening. That lets my team get ahead of the attack and work with other teams to shutter access, de-provision privileges, or undertake other activities to halt the attack.
That information also provides a much more detailed post-mortem than mere access logs. Authorization decision logs highlight where information may have been manipulated or exfiltrated. Combined with other data points, the extent of the impact can be determined with substantial accuracy.
Conclusion
Authorization decision logs provide accurate and detailed information about every action taken within the system for which those logs are being generated. Not every system will have them, but those that do will enjoy a powerful tool to detect potential compromises.
The modern cybersecurity landscape is fraught with danger. The likelihood of being attacked is far greater than ever. The more quantity and quality of information collected about assets within the corporate environment, the more timely and effective are detections and alerts.
Those detections and alerts, in turn, allow security and operational teams to respond to threats. Robust information bolsters those responses.
In short, authorization decision logs promote quick and effective responses which mitigate harm. They do so more effectively than other logs or audit trails in isolation and certainly when correlated with other information.

Aaron Weismann
Contributor, CISO
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)