Feature Review: Decision Logging
May 5th, 2022

Stefan Batres
Feature Review |
Engineering

One of the big benefits of any authorization system is audit trails: information generated by the authorization decisions the system makes, that can be leveraged for many purposes, including compliance. Aserto can collect and manage decision information from all your authorizers, including sidecar and other kinds of locally deployed ones. We call this functionality decision logging.
In this post, we will give an example of how to tap into the data generated by Aserto’s decision logging. But first, let’s take a high-level look at what Aserto decision logging is and how it works.
Decision logging
Aserto authorizers connected to the Aserto control plane participate in decision logging. This includes policy instances Aserto hosts as well as policy instances running in edge authorizers. When one of these authorizers runs the discovery flow, it gets (among other things) decision logging configuration. This configuration can be set on the Aserto console (as well as through the Aserto APIs).
Authorizers that have decision logging turned on will output information about every authorization decision into a local file, which ensures logging occurs even when disconnected. A log shipper component reliably sends the logs to the control plane.
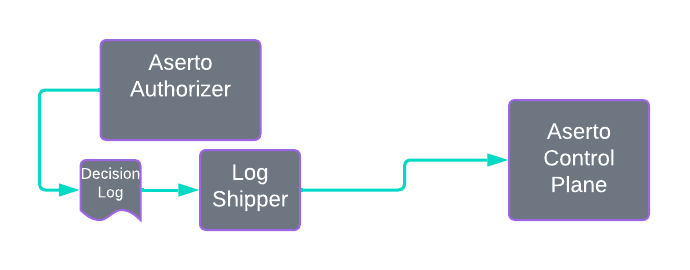
Aserto makes decision logging data available to applications in two ways: First, as a set of bucket storage objects you can download. Aserto keeps up to two weeks of data for you. By using reliable log shippers and bucket storage Aserto can provide strong reliability guarantees for your decision log data.
The second way you can get at your decision log data is via a near real-time data stream you can tap via the Aserto API’s or the Aserto CLI.
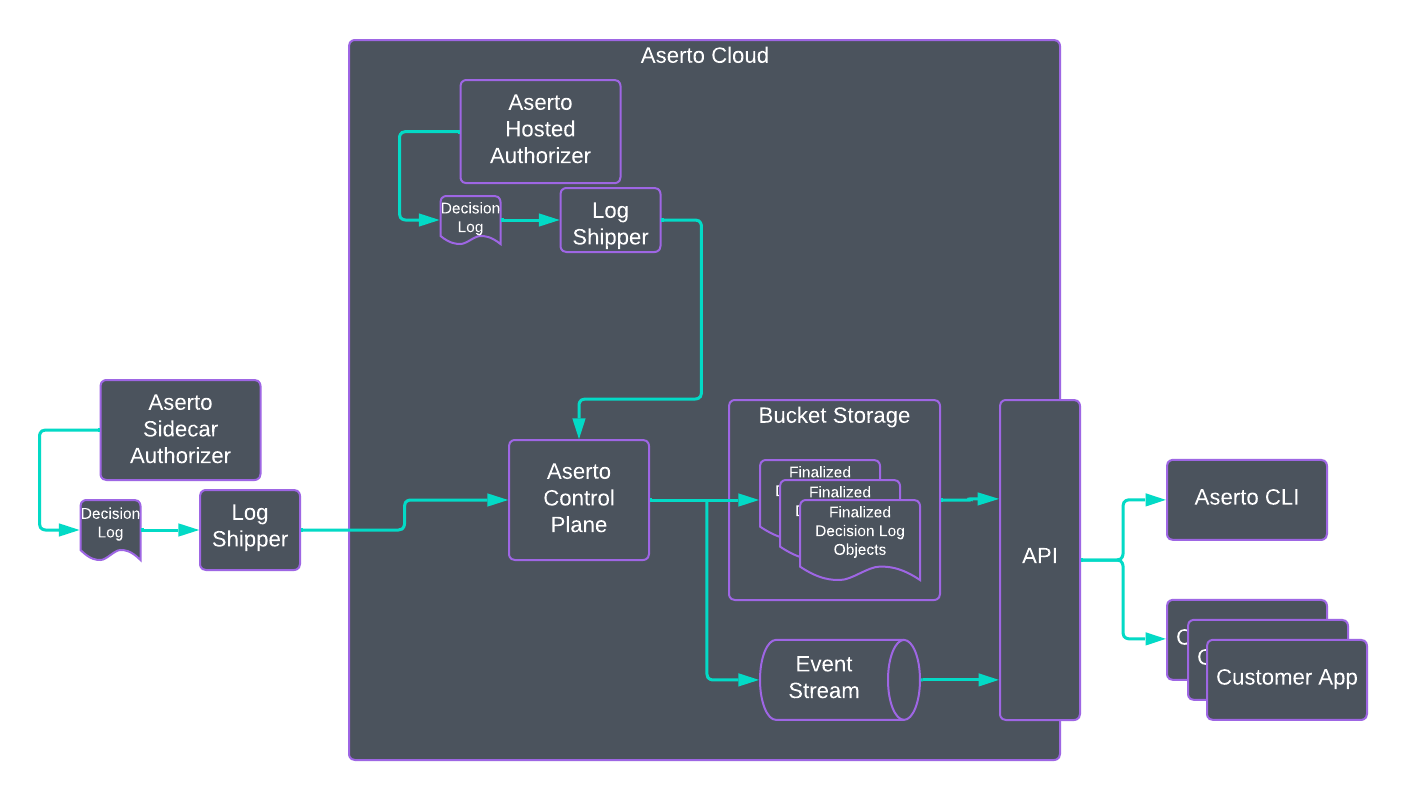
So what data is in decision logs? First, let’s define “decision”: It’s a call to the Aserto authorizer’s Is API. The data included in a decision log, then, is the inputs that generated the decision and the outcomes:
- The policy context; the policy and path to the rule that executed the decision, including the registry and repo where the policy is stored.
- The user context, including the user id.
- The resource context as provided by the application.
- The names of the decisions paired with a boolean outcome for each.
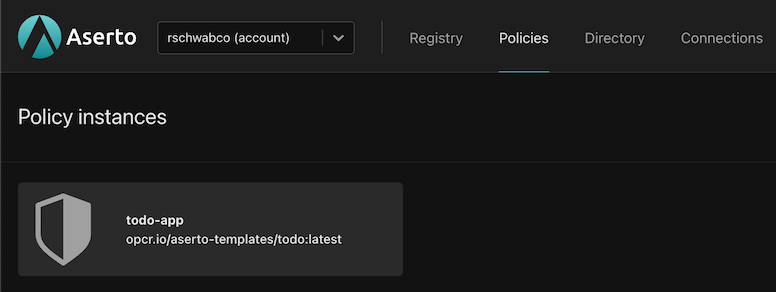
To tap the decision log data first you must turn on decision logging for your policy instance. You can do this on the Aserto console.
Go to the Policies tab and pick a policy instance:
Click the Decision logs tab:
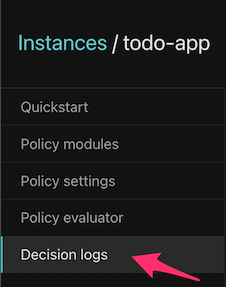
Click the big “Record decision logs” switch:
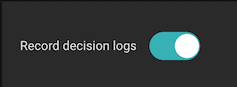
From this point on, decision logs will be generated as your application calls an Aserto authorizer. If you don’t have an application that uses the policy instance, you can exercise it using the Evaluator link on the sidebar. Refresh the list in the decision logs tab to see decisions appear, it might take up to 30s for them to show up.
You can also tap the decision log stream using the Aserto CLI. You can use an API key instead of logging in with your Aserto credentials. The API key is part of the decision logs system connection available in the Aserto console and only allows callers that use it to read decision logs, making it a good choice for automated tools.
You can find the API key in the Connections tab in the Aserto console:
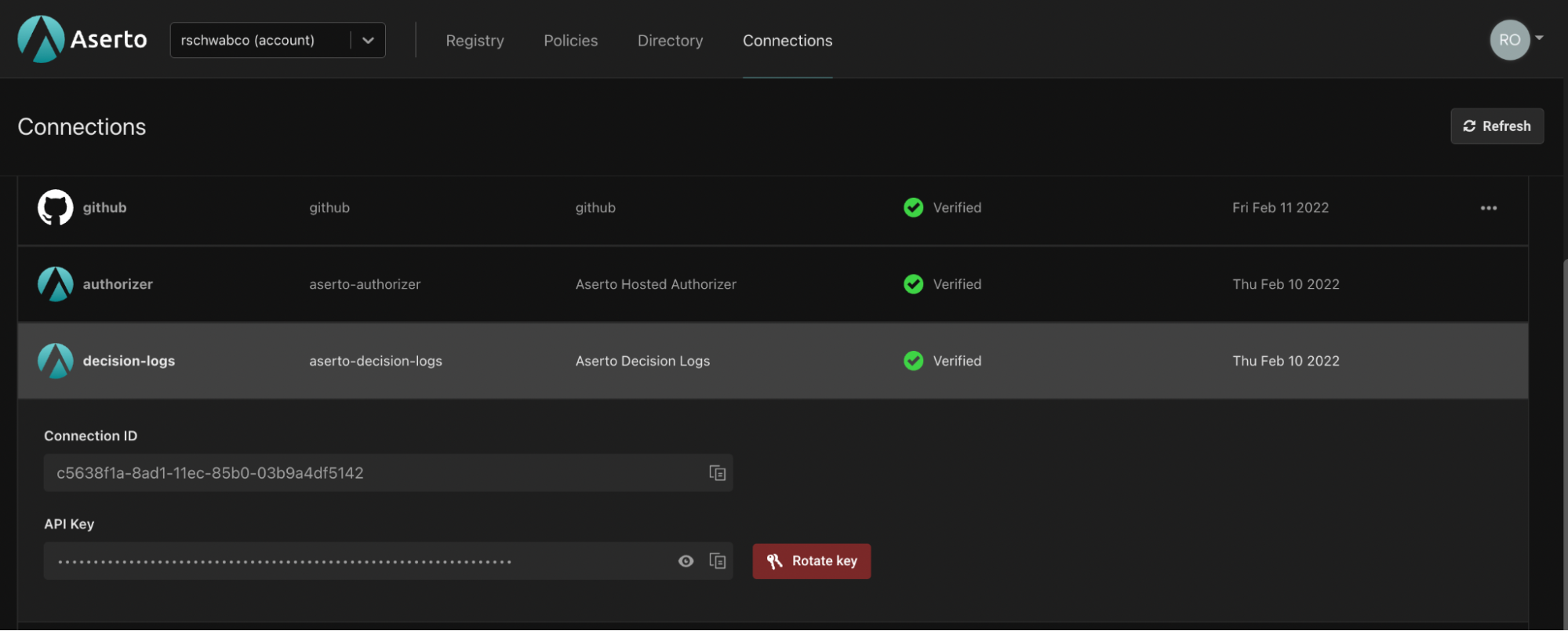
The following Aserto CLI command will retrieve the decision logs stream for you tenant and policy:
aserto l stream –tenant <your tenant id> –api-key <your decision logs api key> <policy id>The CLI will block, listening to the stream, until you unblock it with ctrl-C. The output will contain decisions in JSON format, for example:
{
"id":"5dc1d785-14a5-48ee-9c41-284eaf8c93e9",
"timestamp":{
"seconds":1646245386
},
"path":"peoplefinder.POST.api.users.__id",
"user":{
"id":"1eb018bb-7347-46fd-8d83-35ad5aaa731e",
"email":"scottb@acmecorp.com"
},
"policy":{
"registry_service":"registry.prod.aserto.com",
"registry_image":"stefan/policy-peoplefinder-abac",
"registry_tag":"latest",
"registry_digest":"sha256:5b5dc2b1211682082f8c57f8bce4a7531f17017babf7b8dc90153f160de9744f"
},
"outcomes":{
"allowed":false,
"enabled":false,
"visible":true
},
"resource":{
}
}We hope you find this feature useful! For further information about the decision logs, head to our documentation.

Stefan Batres
Principal Software Engineer
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)