A CISO Perspective on Simplifying Compliance with Decision Logs
Feb 7th, 2023

Aaron Weismann
Security |
Decision Logs
One of the most important functions of any security office is understanding who’s accessing what, when, and if that’s appropriate. From that foundational operation grow numerous other programs: secure authentication, identity governance, data governance, threat management, data loss prevention, and others.
Where those functions are collapsed and automated to implement some kind of XBAC permissions model, authorization decision logs become the critical mechanism for evaluating the correctness of access permissions or troubleshooting access failures.
Let’s dive into what decision logs are and why they’re important to security teams. I’ll then cover why centralized decision logs belong in the “5 laws of authorization.” Then, I’ll conclude with an overview of a couple of compelling solutions and what they accomplish.
What are Authorization Decision Logs?
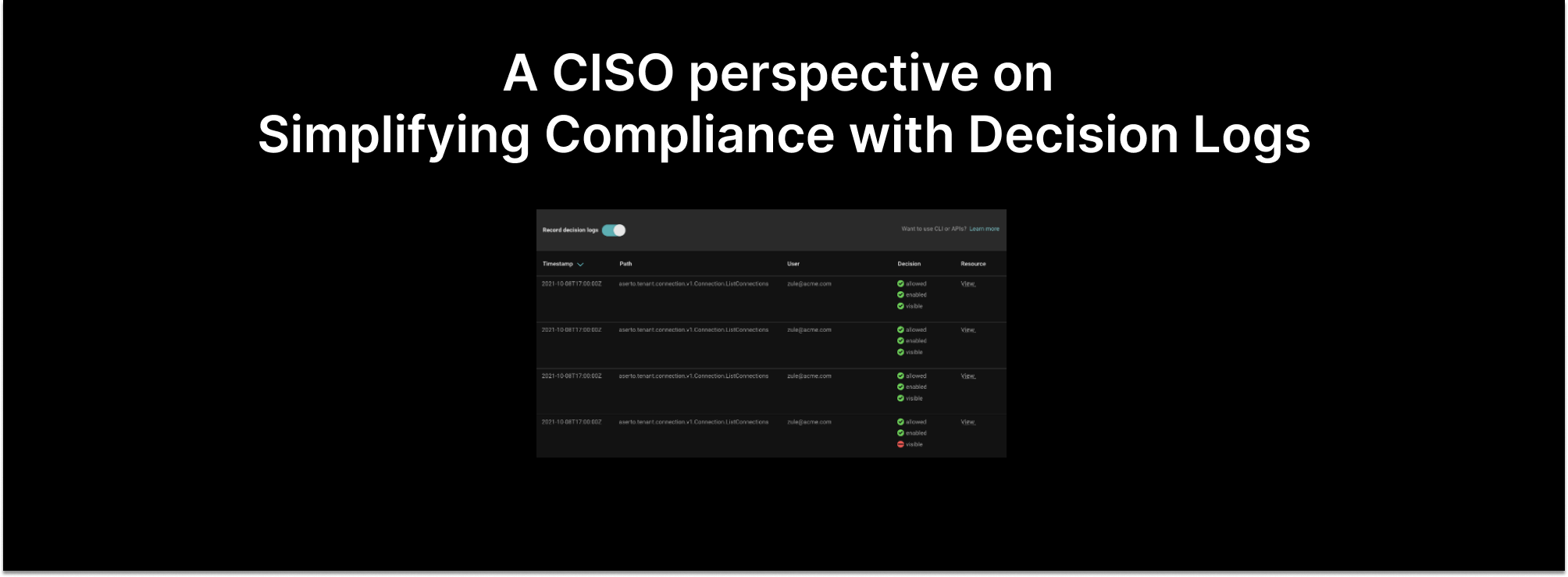
Authorization decision logs are system logs capturing automated access decisions. They are a record of every access decision made for every user once they've logged in. Decision logs are critical for access control systems and enhance the organization’s security posture. They also simplify compliance and boost auditability.
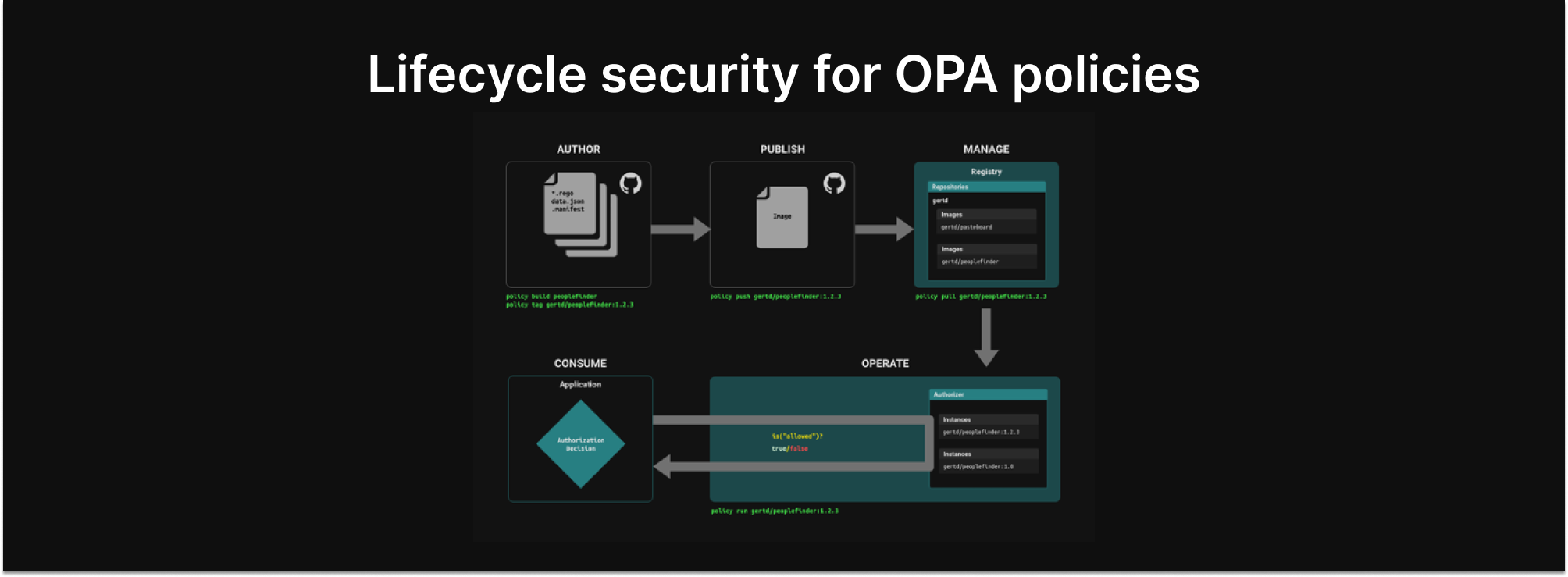
Authorization systems enforce against a policy. Modern applications treat those policies as code that is stored and versioned separately from application code. This means that changes are auditable and published versions can be considered immutable. Those policies are measurable and verifiable, as are changes to those policies. That provides great affirmative security and sets the rules of the road.
Decision logs support the enforcement of those rules, which I’d call defensive security. As rules are utilized and tested, defensive security measures are critical to managing secure access.
Where security policies provide affirmation or rejection of access, they’re not 100% effective 100% of the time. They’re only as good as the logic that captures them, and can be compromised by unintentional functionality or sophisticated threat actors trying to circumvent them.
Capturing and scanning decision logs provides an additional, reactive layer of defense, to detect inappropriate levels of access.
Auditability and Ease of Compliance
Robust auditing bolsters and supplements security. The auditing function, whether automatic by a SIEM, XDR, or other log aggregation tool or by independent verification and validation of controls, validates that authorizations are appropriate every time. This is also a common requirement for compliance. It’s an affirmative but reactive control that allows course correction should authorization go awry.
To perform that auditing, there needs to be a strong record of the authorization process. Logging every authorization decision provides that strong record. This allows for the evaluation of every decision. And the evaluation provides a common baseline for "appropriate" and "inappropriate" authorization behavior.
It also transforms compliance into a binary exercise. Either an individual should or should not have access to resources based on specific conditions. They either are or are not provided access. The automated decisions system will enforce and log that.
That system works for compliance schemes that are well-defined and not prone to exception. For example, if a HIPAA Covered Entity determines a class of staff should not have access to PHI in specific assets, then access to that PHI should never be authorized.
By centralizing logs about those kinds of authorization decisions, organizations raise confidence in events that could otherwise erode that confidence. Misapplied authorization means that something isn’t working with an asset’s authorization logic or policy. Or it may mean that the authorization decision was otherwise overridden. Centralizing decision logs help the organization become and remain compliant by alerting to deviations in authorization.
Centralized Decision Logs as Part of 5 Laws of Authorization
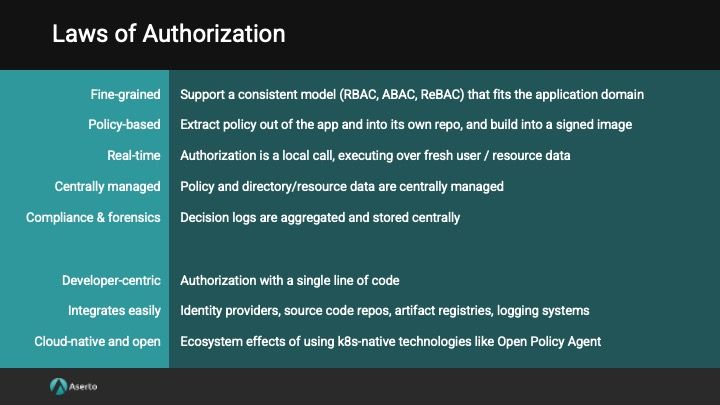
The Aserto 5 Laws of Authorization are an interesting artifact. They provide a synopsis of best practices for cloud-native applications and incorporate both OWASP and MITRE ATT&CK. They also outline how to accomplish those with open-source tools.
Centralized decision logs as a domain is one of the key concepts promoted as part of the 5 Laws of Authorization. That acknowledges how important it is as a best practice and how recommended the practice comes from security frameworks.
Log aggregation and management allows a security team to act and react based on that information to address breaches. Centralizing logs facilitates the best practice of comprehensive monitoring.
It’s impossible for events to be actionable without logs. It’s difficult for logs to be effectively used when located in disparate places and manually correlated, if even correlated at all.
Efficiency, effectiveness, and actionability all demand the centralization of decision logs with other log information. All organizations can benefit from the centralization of decision logs if they need to troubleshoot access issues with assets or address potential cyber threats.
Centralized aggregation of decision logs is also necessary for regulated critical infrastructure like the financial and healthcare sectors. Where the lives and livelihoods of millions of patients, investors, customers, or clients can be negatively impacted by a cyberattack, identifying threats quickly and terminating them is a must.
That quick and effective threat hunting is impossible without centralized decision logs. Failing to facilitate that kind of quick and effective threat-hunting is downright reckless in 2023 when there are daily reminders of the consequences of cyberattacks.
Decision Log Centralization Solutions
A few decision log centralization solutions exist and all have their pros and cons. Depending on your infrastructure and the number of legacy assets you have, you may be forced to use one method over another. As long as you do something to centralize your decision logs, you’re being proactive against cyber threats.
If you’re using a traditional SIEM solution, you’re familiar with the concept of heavy forwarders. These are apps that sit on servers that correlate log data for ingestion by a cloud or on-premises instance. They’re effective, but they’re not particularly resource efficient.
They’re also not particularly effective for serverless infrastructure. For that, the SIEM solution either relies on platform telemetry or integrated plugins purpose-built for that environment. Fortunately, many SIEM providers are on board with that and have developed the infrastructure needed to accommodate visibility.
SIEMs can also ingest logs for authorization decision engines, but require the ability to gather data from that decision engine and appropriate formatting to correlate data. That formatting can be addressed in the SIEM instance, but it’s easier to pre-format that information elsewhere. That’s especially true if that information is being pulled from many authorizers based on the same access policies.
One solution that manages both granular authorization and centralizes decision logs with consistent formatting and easy ingestion is Aserto. It facilitates XBAC–RBAC, ABAC, or ReBAC– authorization modeling. It also provides uniform decision logs for every authorization decision made. Decision logs are centralized and easily shared with logging systems and SIEM tools.
Overall, this solution appears to promote transparency and interoperability. That’s key for infrastructure and application management teams who need easy access to information to make informed troubleshooting and threat-hunting determinations.
Conclusion
Driving compliance, or managing risk, is key for any organization that wants to minimize the possibility of a cyberattack. For regulated organizations upon which people’s lives and livelihoods depend, competent cybersecurity is a must.
Competent cybersecurity demands the centralization of all logs, but especially authorization decision logs. Knowing who is accessing what, when and why is critical to safeguarding your assets and data. It’s also important to know why access was not provided for potential troubleshooting purposes.
Many SIEM and XDR solutions provide log aggregation and collection solutions, but they do not provide access control logs. Aserto helps with that. Aggregating fine-grained authorization functionality, policy management, and detailed decision log reporting into one solution.

Aaron Weismann
Contributor, CISO
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)