Authorization for Identity Providers and Single Sign-on
Enterprise-grade authorization for identity providers
SSO identity providers
An identity provider (IDP) is a system that creates, maintains, and manages identity information. Identity providers offer user authentication as a service and let end users use single sign-on (SSO) to access other websites and applications.
Single sign–on is an authentication method that allows users to sign-in using one set of credentials to multiple independent websites and software services. Cloud platforms offer identity services and standards like OAuth2, OpenID Connect, SAML, and JWT to create an interoperable identity fabric. Authentication-as-a-service companies like Okta, Auth0,, PingID, and OneLogin take advantage of these standards and provide cross-platform SSO services spanning a variety of identity providers.
SSO provides better security by decreasing the potential attack surface while reducing password fatigue. IDPs enable SSO as part of their identity authentication toolset, which also includes data protection, and password management.
Identity provider authorization
Authorization is a different challenge than authentication. Authentication answers the question of “who is trying to access the service?” Authorization answers the question “which users can access what resources?” While authentication happens once per session, authorization happens in response to every request. As a result, there are a number of unique requirements when adding authorization to your identity provider:
- Seamless integration with your IDP and existing authentication system by accepting information in a cryptographic token such as a Javascript web token (JWT)
- Automatic mapping of user attributes from your IDP (Google, Azure AD, Amazon Cognito, Okta, Auth0) and enterprise directories (Active Directory, LDAP) to authorization policies
- A standardized policy-building language
- Processing policy decisions with minimal latency and the same availability as your application
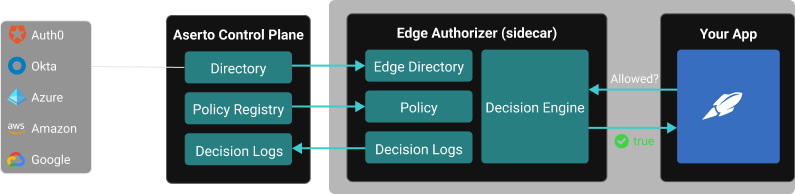
Aserto adds authorization as a service to your application and seamlessly integrates with your IDP to push user information to the authorizers that sit at the edge of your application.
How it works
At runtime, your IDP will send your application a signed access token and authenticate a user. Before accessing a resource within your app, it will make a call to the Aserto edge authorizer deployed next to your application as a microservice or sidecar. The user context, policy context, and resource context from your application are then fed to the authorizer, and the request is then gated by the authorization decision produced by the OPA engine.Any changes made to your IDP’s directory will be automatically synchronized into Aserto and then pushed to the edge authorizer in near real-time.
Leveraging the policy, user, and resource contexts, Aserto is built to be flexible and so it evolves with the needs of your application. You can transition from coarse-grained role-based access control (RBAC) to fine-grained authorization using attribute-based access control (ABAC), access-control lists (ACL), or a mix of any of the three in order to meet your requirements as the needs of your customers evolve.
Plugging your authentication solution into Aserto allows you to bridge the gap between authentication and authorization creating an end-to-end Auth solution.
Aserto also comes with the following benefits:
- Out-of-the-box support for audit trails, custom roles, RBAC, ABAC, and ACL
- Use a policy-as-code workflow to build, tag, push, version, and pull policy images just like docker images
- Quick onboarding via first-class citizen integrations with Auth0 and your artifact registry, logging system, backend programming language, and frontend framework.
- Built on top of a trusted open source policy engine, the Open Policy Agent (OPA)

&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)











