Authorization service for Auth0

Enterprise-grade authorization for Auth0
About the integration
Auth0 is an adaptable authentication platform that lets you easily add authentication to your application. Aserto is a powerful authorization service that enables you to determine permissions and access within your application. Together, they provide out-of-the-box solutions for user authentication and authorization.
About Auth0
Auth0 is a flexible user authentication platform you can use as a complete login solution for your application. It provides the tools necessary to develop and maintain a secure identity infrastructure, including user authentication, data protection, and password management.
With Auth0, you can easily implement single sign-on (SSO), multi-factor authentication (MFA), universal login, or passwordless access to your application via the platform’s robust API. It makes implementing token-based authentication, email provider authentication, social network authentication, multi-factor authentication, and forget/change password flows a breeze.
About Aserto
Aserto is a powerful and flexible authorization-as-a-service built to evolve with your customer requirements. It helps you define, evolve, and enforce user permissions within your application.
Aserto is the perfect complement to Auth0’s authentication solution: Aserto makes it easy to define and evolve what users are permitted to do inside your applications. Built on trusted open-source projects like OPA and OCI, Aserto handles all the heavy lifting required to achieve secure, scalable, high-performance role-based access control (RBAC), attribute-based access control (ABAC), and relationship-based access controls (ReBAC).
Aserto natively integrates with Auth0, and is typically incorporated into applications in under a day. Quickstarts and SDKs are available for popular programming languages and frameworks, including Node.js, Golang, Python, JavaScript, ASP.Net, Java, Ruby and React, helping you get up and running in little to no time. REST, gRPC, and GraphQL APIs are available for developers that want to go to the metal.
Better together
Setting things up
To set things up, connect Aserto to your Auth0 tenant, to import and automatically synchronize the users, roles, and attributes stored in your Auth0 tenant into the Aserto directory. You’ll also define your permissions and authorization policies in Aserto, and load any resource data you want to use in your authorization decisions.
You can develop against Aserto’s hosted authorizer, which Aserto operates for you. In a production system, you should deploy Aserto authorizers right next to your application, either as a sidecar or a microservice in the same cluster or subnet. Aserto’s control plane automatically syncs any changes to user, resource, or policy data with everu connected authorizer in near real time, ensuring you authorize based on the most up-to-date information.
At runtime
At runtime, your application should verify the signed access token it receives from Auth0 after the user authenticates. Before accessing a protected resource, your application should make a call to the Aserto Authorizer, passing it the user context (typically in the form of the access token), policy context, and resource context. The Aserto Authorizer uses the powerful OPA decision engine to make an authorization decision in milliseconds based on this data, which the application can use in order to gate the request and fail it if the user is not authorized to make it.
Auditing authorization decisions
Aserto captures a record of every authorization decision in a decision log for easy auditing from the control plane. Decision logs can be streamed or batched up into your favorite log analysis tool, or SIEM.
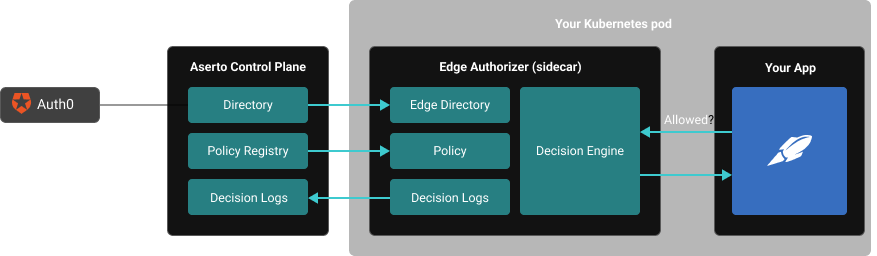
The Authorizer architecture
While authentication happens once per session, authorization is on the critical path of every request, so speed of response is critical. Aserto authorizers are deployed as microservices or sidecars right next to your application to minimize authorization latency and maximize availability. That way, your application is never dependent on the availability / uptime of a remote authorization service.
The authorizers make decisions based on three important inputs:
- Policies from your policy registry
- Users, attributes, and roles from Auth0, supplemented with application-specific information stored in the Aserto directory
- Resource context passed by in your application
Any changes made to your Auth0 directory are automatically synced with the Aserto directory, to ensure you never make authorization decisions based on stale data. Aserto then pushes updates to your local authorizers in near real time, or can be configured to update on an interval determined by the application administrator.
Leveraging the policy, user, and resource contexts, makes it easy to evolve your authorization from coarse-grained RBAC to fine-grained authorization using attributes (ABAC), relationships (ReBAC), or a combination to meet your requirements as they evolve. This means you can build a strong authorization foundation once, and seamlessly evolve your access control model when needed.
Integrating Auth0 with Aserto allows you bridge the gap between authentication and authorization creating an end-to-end Auth solution.
Aserto also comes with the following benefits:
- Out-of-the-box support for audit trails, custom roles, RBAC, ABAC, and ReBAC
- Open-source authorizer you can deploy in your cloud today
- Use a policy-as-code workflow to build, tag, push, version, and pull policy images just like docker images
- Quick onboarding via first-class citizen integrations with Auth0 and your artifact registry, logging system, backend programming language, and frontend framework.
- Built on top of a trusted open source policy engine, the Open Policy Agent (OPA)
Resources

&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)











